How to remove Apple Security Alert from Mac?
Remove 'apple support alert' virus related Safari extensions: Open Safari browser, from the menu bar, select ' Safari ' and click ' Preferences.' In the preferences window, select ' Extensions ' and look. 4 hours ago Cult of Mac - iPhone users should install iOS 14.4.1, which was released on Monday entirely to kill a bug in the Safari web browser. Obviously, Apple considers it a significant enough threat to.
- Alerts provide timely information about current security issues, vulnerabilities, and exploits. Sign up to receive these technical alerts in your inbox or subscribe to our RSS feed.
- Explore the web knowing that strong security protections in Safari help keep you safe. Like iCloud Keychain, which securely stores and autofills your passwords across all your devices. If a password breach is detected, Password Monitoring alerts you.
- The official looking alert, which is presented in a native iOS alert housing, pops up randomly in Safari and attempts to convince the user that the device has crashed “due to a third party application in.
What is Apple Security Alert?
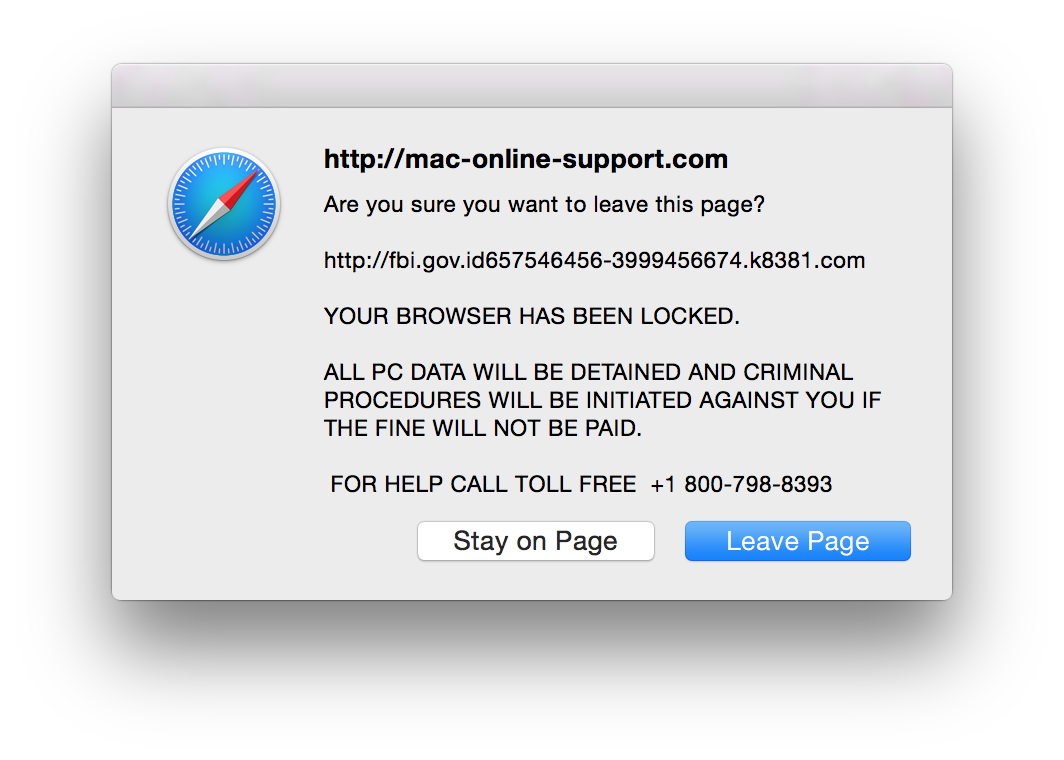
Displayed by a malicious website, 'Apple Security Alert' is a fake pop-up error similar to Apple Support Center - Attention!!, Apple Warning Alert, Critical Security Warning!, and many others. Users often visit this website inadvertently - they are redirected by variety of potentially unwanted programs (PUPs). Research shows that as well as causing redirects, rogue programs misuse computer resources, deliver malicious ads, and record various data.
The 'Apple Security Alert' error states that the system is infected and the user's account has been hacked. In addition, private information is at risk. Therefore, the user should immediately contact iOS Tech Support via a telephone number ('1-855-633-1666') provided. Certified technicians then supposedly guide users through the malware removal process. Note, however, that 'Apple Security Alert' is fake and has nothing to do with Apple. Cyber criminals generate revenue by scaring and tricking unsuspecting users into paying for technical support that is not required. The malware simply does not exist. These people often demand remote access to the computer. They do this to stealthily modify system settings and/or install various malware. Criminals then claim to 'find' additional issues/errors and offer their help for an additional fee. Therefore, never contact these people. 'Apple Security Alert' can be removed by closing the web browser or rebooting the system. Be aware that fake error-displaying websites and potentially unwanted programs often misuse system resources to run unwanted processes (e.g., mining cryptocurrency) in the background. This behavior significantly diminishes system performance. Furthermore, potentially unwanted programs often deliver various 'malvertising' ads (pop-ups, coupons, banners, etc.) using various tools that enable placement of third party graphical content on any site. Therefore, displayed ads often conceal underlying content. These ads might redirect to malicious websites and/or execute scripts designed to download/install malware - clicking them risks further computer infections. Potentially unwanted programs are also known to record various data types (e.g., IP addresses, URLs visited, search queries, keystrokes, etc.) that might contain personal details. This data is sold to third parties (mostly, for marketing purposes). Potentially unwanted programs pose a direct threat to your privacy and Internet browsing safety. Therefore, uninstall all PUPs immediately.
| Name | 'Apple Security Alert' virus |
| Threat Type | Mac malware, Mac virus |
| Symptoms | Your Mac became slower than normal, you see unwanted pop-up ads, you get redirected to shady websites. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake flash player installers, torrent file downloads. |
| Damage | Internet browsing tracking (potential privacy issues), displaying of unwanted ads, redirects to shady websites, loss of private information. |
| Malware Removal (Mac) | To eliminate possible malware infections, scan your Mac with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
As mentioned above, 'Apple Security Alert' shares many similarities with dozens of other fake errors that also claim that the system is damaged. In fact, these errors are designed only to extort money from unsuspecting users. Potentially unwanted programs also share similarities. Most claim to enable 'useful functions' (e.g., increase download performance, remove viruses, optimize media files without diminishing quality, etc.), however, these false claims are merely attempts to give the impression of legitimacy. PUPs are designed only to generate revenue for the developers. Only a small percentage of these apps enable the functionality promised - most cause redirects, diminish system performance, generate ads, and gather information.
How did potentially unwanted programs install on my computer?
Some PUPs have official download websites, however, most are promoted using malicious ads together with a deceptive marketing method called 'bundling'. Therefore, PUPs often infiltrate systems without permission, or users install them inadvertently, without their consent. Bundling is stealth installation of third party software together with regular (mostly, free) apps. Developers are aware that users often rush the download/installation processes and skip steps. Therefore, they hide bundled apps within various sections (usually the 'Custom/Advanced' settings) of these processes. By rushing, users expose their systems to risk of various infections and compromise their privacy.
How to avoid installation of potentially unwanted applications?
Be very careful when browsing the Internet and especially when downloading/installing software. Most malicious ads appear genuine, however, they are distinguishable for their redirects - most lead to pornography, adult dating, gambling, survey, and other dubious sites. If you encounter such ads, uninstall all suspicious applications and browser plug-ins. Furthermore, closely study each download and installation step (including 'Custom/Advanced' settings) and cancel all additionally-included programs. Note that third party download/installation tools are monetized by promoting malicious apps (the bundling method) and should, thus, never be used. Poor knowledge of these threats and rushing steps are the main reasons for computer infections - the key to safety is caution.
Text presented within 'Apple Security Alert' pop-up:
Apple Security Alert- Warning iOS - Crash Report Suspicious Activity Detected
Error code: appdel001
Malicious application detected by apple scan and there has been a hacking alert on your account. Your personal and financial information is at risk major security issue.
Contact our iOS Tech Support for an immediate fix
+1-855-633-1666(Toll Free)!
Appearance of 'Apple Security Alert' scam (GIF):
Text presented within this pop-up:
Virus Alert
Your device might be infected. Call the toll free number to resolve this problem 1-855-633-1666
Another example of 'Apple Security Alert' pop-up scam:
Text presented within:
macOS Security
Apple Security Alert - Error Code: #0x83d47d
Access to this PC has been blocked for security reasons.
Contact Mac Support: +1-888-599-2660 (Toll Free)
Threat Detected - Trojan Spyware
App: Ads.financetrack(1).exe
[Run Anyway] [Back to Safety]
Instant automatic Mac malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced computer skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of Mac malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner for MacBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
Quick menu:
- STEP 1. Remove PUP related files and folders from OSX.
- STEP 2. Remove rogue extensions from Safari.
- STEP 3. Remove rogue add-ons from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins from Mozilla Firefox.
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted programs removal:
Remove PUP-related potentially unwanted applications from your 'Applications' folder:
Click the Finder icon. In the Finder window, select “Applications”. In the applications folder, look for “MPlayerX”,“NicePlayer”, or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited three days free trial available.
Remove 'apple security alert' virus related files and folders:
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
Check for adware-generated files in the /Library/LaunchAgents folder:
In the Go to Folder... bar, type: /Library/LaunchAgents
In the “LaunchAgents” folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, “kuklorest.update.plist”, etc. Adware commonly installs several files with the same string.
Check for adware generated files in the /Library/Application Support folder:
In the Go to Folder... bar, type: /Library/Application Support
In the “Application Support” folder, look for any recently-added suspicious folders. For example, “MplayerX” or “NicePlayer”, and move these folders to the Trash.

Check for adware-generated files in the ~/Library/LaunchAgents folder:
In the Go to Folder bar, type: ~/Library/LaunchAgents
In the “LaunchAgents” folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - “installmac.AppRemoval.plist”, “myppes.download.plist”, “mykotlerino.ltvbit.plist”, “kuklorest.update.plist”, etc. Adware commonly installs several files with the same string.
Check for adware-generated files in the /Library/LaunchDaemons folder:
In the Go to Folder... bar, type: /Library/LaunchDaemons
In the “LaunchDaemons” folder, look for recently-added suspicious files. For example “com.aoudad.net-preferences.plist”, “com.myppes.net-preferences.plist”, 'com.kuklorest.net-preferences.plist”, “com.avickUpd.plist”, etc., and move them to the Trash.
Scan your Mac with Combo Cleaner:
If you have followed all the steps in the correct order you Mac should be clean of infections. To be sure your system is not infected run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file double click combocleaner.dmg installer, in the opened window drag and drop Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates it's virus definition database and click 'Start Combo Scan' button.
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays 'no threats found' - this means that you can continue with the removal guide, otherwise it's recommended to remove any found infections before continuing.
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
'Apple Security Alert' virus removal from Internet browsers:
Remove malicious extensions from Safari:
Remove 'apple security alert' virus related Safari extensions:
Open Safari browser, from the menu bar, select 'Safari' and click 'Preferences...'.
In the preferences window, select 'Extensions' and look for any recently-installed suspicious extensions. When located, click the 'Uninstall' button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
Remove malicious plug-ins from Mozilla Firefox:
Remove 'apple security alert' virus related Mozilla Firefox add-ons:
Open your Mozilla Firefox browser. At the top right corner of the screen, click the 'Open Menu' (three horizontal lines) button. From the opened menu, choose 'Add-ons'.
Choose the 'Extensions' tab and look for any recently-installed suspicious add-ons. When located, click the 'Remove' button next to it/them. Note that you can safely uninstall all extensions from your Mozilla Firefox browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Remove malicious extensions from Google Chrome:
Remove 'apple security alert' virus related Google Chrome add-ons:
Open Google Chrome and click the 'Chrome menu' (three horizontal lines) button located in the top-right corner of the browser window. From the drop-down menu, choose 'More Tools' and select 'Extensions'.
In the 'Extensions' window, look for any recently-installed suspicious add-ons. When located, click the 'Trash' button next to it/them. Note that you can safely uninstall all extensions from your Google Chrome browser - none are crucial for normal browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
Safari 6.0.5 can be downloaded and installed via Software Update preferences, or from Apple Downloads.
For the protection of our customers, Apple does not disclose, discuss, or confirm security issues until a full investigation has occurred and any necessary patches or releases are available. To learn more about Apple Product Security, see the Apple Product Security website.
For information about the Apple Product Security PGP Key, see 'How to use the Apple Product Security PGP Key.'
Safari Security Alert Ipad
Where possible, CVE IDs are used to reference the vulnerabilities for further information.
To learn about other Security Updates, see 'Apple Security Updates.'
Safari 6.0.5
WebKit
Available for: OS X Lion v10.7.5, OS X Lion Server v10.7.5, OS X Mountain Lion v10.8.3
Impact: Visiting a maliciously crafted website may lead to an unexpected application termination or arbitrary code execution
Description: Multiple memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
CVE-ID
CVE-2013-0879 : Atte Kettunen of OUSPG
CVE-2013-0991 : Jay Civelli of the Chromium development community
CVE-2013-0992 : Google Chrome Security Team (Martin Barbella)
CVE-2013-0993 : Google Chrome Security Team (Inferno)
CVE-2013-0994 : David German of Google
CVE-2013-0995 : Google Chrome Security Team (Inferno)
CVE-2013-0996 : Google Chrome Security Team (Inferno)
CVE-2013-0997 : Vitaliy Toropov working with HP's Zero Day Initiative
CVE-2013-0998 : pa_kt working with HP's Zero Day Initiative
CVE-2013-0999 : pa_kt working with HP's Zero Day Initiative
CVE-2013-1000 : Fermin J. Serna of the Google Security Team
CVE-2013-1001 : Ryan Humenick
CVE-2013-1002 : Sergey Glazunov
CVE-2013-1003 : Google Chrome Security Team (Inferno)
CVE-2013-1004 : Google Chrome Security Team (Martin Barbella)
CVE-2013-1005 : Google Chrome Security Team (Martin Barbella)
CVE-2013-1006 : Google Chrome Security Team (Martin Barbella)
CVE-2013-1007 : Google Chrome Security Team (Inferno)
CVE-2013-1008 : Sergey Glazunov
CVE-2013-1009 : Apple
CVE-2013-1010 : miaubiz
CVE-2013-1011 : Google Chrome Security Team (Inferno)
CVE-2013-1023 : Google Chrome Security Team (Inferno)
WebKit
Available for: OS X Lion v10.7.5, OS X Lion Server v10.7.5, OS X Mountain Lion v10.8.3
Impact: Visiting a maliciously crafted website may lead to a cross-site scripting attack
Description: A cross-site scripting issue existed in the handling of iframes. This issue was addressed through improved origin tracking.
CVE-ID
CVE-2013-1012 : Subodh Iyengar and Erling Ellingsen of Facebook
WebKit
Available for: OS X Lion v10.7.5, OS X Lion Server v10.7.5, OS X Mountain Lion v10.8.3
Impact: Copying and pasting a malicious HTML snippet may lead to a cross-site scripting attack
Description: A cross-site scripting issue existed in the handling of copied and pasted data in HTML documents. This issue was addressed through additional validation of pasted content.
CVE-ID
CVE-2013-0926 : Aditya Gupta, Subho Halder, and Dev Kar of xys3c (xysec.com)
What Does Apple Security Alert Mean
Safari Security Settings
WebKit
Available for: OS X Lion v10.7.5, OS X Lion Server v10.7.5, OS X Mountain Lion v10.8.3
Impact: Following a maliciously crafted link could lead to unexpected behavior on the target site
Description: XSS Auditor may rewrite URLs to prevent cross-site scripting attacks. This may lead to a malicious alteration of the behavior of a form submission. This issue was addressed through improved validation of URLs.
CVE-ID
CVE-2013-1013 : Sam Power of Pentest Limited